Explain Different Types of Online Threats Class 10
If you do any online banking stock trading or make other sensitive online transactions you should exercise extra care. The main types of cyber threats are.

10 Essential Cybersecurity Tips For Businesses Cyber Security Technology Cyber Security Awareness Cyber Security
Information Security threats can be many like Software attacks theft of intellectual property identity theft theft of equipment or information sabotage and information extortion.

. Threats to Information Security. The aim of this study was to identify the strengths weaknesses opportunities and threats SWOT of BL in a premedical class. A computer threat can be intentional such as hacking or accidental such as malfunctioning of or physical damage.
A direct threat identifies a specific target and is delivered in a straightforward clear and explicit manner. Distributed denial of service DDoS Man in the Middle MitM Social engineering. Here are the top 10 threats to information security today.
What are the main types of cybersecurity threats. Up to 20 cash back Web Threats. Verbal physical and social bullying can happen in person.
Unsafe surfing can also lead to other threatsfrom embarrassing personal comments or images that once online are nearly impossible to erase to getting mixed up with people youd rather have had nothing to do with. Biodiversity is a reservoir of resources for the manufacture of food cosmetic products and pharmaceuticals. Mobile Device Security Threats.
Crops livestock fishery and forests are a rich source of food. Protect Sensitive Personal Information. Short for malicious software malware comes in several forms and can cause serious damage to a computer or corporate network.
Advanced persistent threats APT We cover each of these threats in more detail below. Web-based threats or online threats are malware programs that can target you when youre using the Internet. A Trojan horse varies from a virus because the Trojan binds itself to non-executable files such as image files audio files.
Phishing attacks are social engineering attacks and they can have a great range of targets depending on the attacker. A veiled threat is one that strongly implies but does not specifically threaten violence. Following are the most common types of computer threats.
A Trojan horse is malware that carries out malicious operations under the appearance of a desired operation such as playing an online game. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world. Network-based threats are especially common and risky because cybercriminals can steal unencrypted data while people use public WiFi networks.
New technology is being released every day. Physical damage It includes fire water pollution etc. Trojan horse.
The plan the intended victim the motivation and other aspects of the threat are masked or equivocal. It was a cross-sectional study. A common delivery method is to include malicious scripts in an attachment of a familiar type like a Word document PDF file or PowerPoint presentation.
In order to protect yourself you need to know about the different ways in which your computer can be compromised and your privacy infringed. 5 Most Common Types of Threats You Need to Know About. Unsuspecting readers who click on a link or open an email attachment end up with some type of malware including ransomware Trojans bots info-stealers cryptominers spyware and keyloggers.
Dont access your accounts. Natural events It includes climatic earthquake volcanic activity etc. Wood fibres perfumes lubricants rubber resins poison and cork are all derived from.
Learners represent different generations different personality types and. Protecting business data is a growing challenge but awareness is the first step. Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter erase harm object or objects of interest.
Technology with Weak Security. An indirect threat tends to be vague unclear and ambiguous. The 12 types of Cyber Crime.
They could be generic scam emails looking for anyone with a PayPal account. Mobile Network Security Threats. The main tool behind such browser-based infections is the exploit pack which gives cybercriminals a.
Wild plants such as Cinchona and Foxglove plant are used for medicinal purposes. Here are the Top 10 Internet safety rules to follow to help you avoid getting into trouble online and offline. Phishing can also be a targeted attack focused on a specific individual.
Online bullying is sometimes called cyberbullying. These browser-based threats include a range of malicious software programs that are designed to infect victims computers. Distributed denial of service DDoS.
Physical threats to mobile devices most commonly refer to the loss or theft of a device. Biological diversity largely describes the change of life from genes to ecosystems comprising their existences genetic variations their environment populations and the ecosystem in which they are existing and other evolutionary developments that keep the system functioning changing and adapting. Specific features of online settings create additional concern for students parents and carers and teachers.
Verbal and social bullying can happen online as can threats of physical bullying. Ninety six students in a premedical cell biology class participated in the study. Different kinds of online threats.
Up to 20 cash back What are the different types of phishing attacks.

Mobile Security Tips Mobile Security Computer Security Security Tips
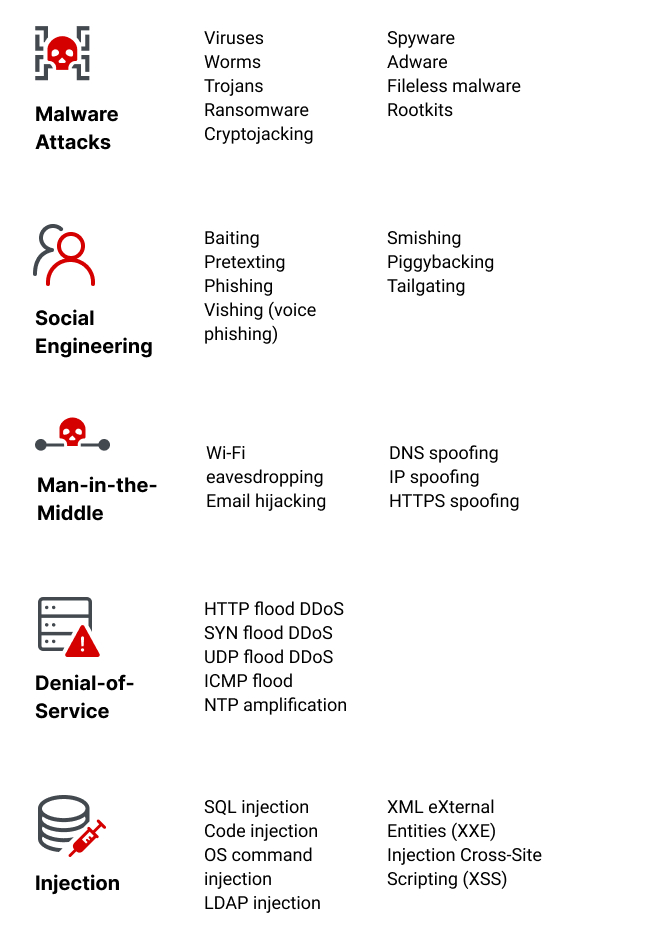
Cyber Security Threats Types Sources Imperva

Ransomware Attacks Are The Fastest Growing Malware Threats Ransomware A Type Of Malicious Software That Infects And Restric Malware Removal Malware Computer

10 Types Of Identity Theft You Should Know About Info Savvy Identity Theft Identity Competitive Intelligence

Cyber Security Its Types And Advantages Cyber Security Technology What Is Cyber Security Cyber Security Education

The Basics Of Cyber Security Visual Ly Cyber Security Technology Computer Security Cyber Security Awareness

The Ultimate Privacy Guide For Mac Users Cyber Attack Tor Browser Popular Search Engines

What S Sql Injection Different Types Of Attacks And How Can An Attack Be Prevented Sql Sql Injection Injections

7 Types Of Cyber Security Threats

Network Security Threats 5 Ways To Protect Yourself

Cybersecurity Our Favorite Articles And Tips Drivesavers Data Recovery Services Cyber Security Electronic Data Systems Wordpress Security

Top 10 Common Network Security Threats Explained

10 Tips On Making Your Employees Care About Cyber Security Awontis Cyber Security Cyber Awareness Cybersecurity Infographic

10 Common Internet Security Threats And How To Avoid Them

Cyber Security Infographic Template Cybersecurity Infographic Cyber Security Free Infographic Templates



